SHARKSSL FREE DOWNLOAD
In step 5, we convert an X. Available as source code, SharkSSL code can be implemented on any processor off the shelf. This site uses cookies. The IDE provides a complete development environment with no other tools required! The following code snippet shows how to create a SharkSslCon instance after you have created a new socket connection. We recommend reading our certificate management tutorial if you are new to certificates.
| Uploader: | Maunos |
| Date Added: | 22 January 2006 |
| File Size: | 35.50 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 3360 |
| Price: | Free* [*Free Regsitration Required] |
The following two examples, which are accompanied by our Securing Edge Nodes Whitepapershow how to use RayCrypto for signing and verifying binaries such as firmware.
These buffers can be used for creating a zero copy API for your network program. The input buffer is designed such that it can dynamically grow if it is not sufficiently large enough for the incoming message.
You must make sure you enter your shatkssl The function may for example detect a button click and return. The online benchmark above includes some of our ciphers. Returns the last time the session was accessed. Out-of-the-box support for uIP and lwIP in event driven mode.

We recommend reading our certificate management tutorial if you are new to certificates. SharkSSL-Lite includes a limited set of ciphers.
Download SharkSSL Eval Kits
The name is presented by UI. All example code delivered with SharkSSL uses this library. The WebSocket LED Server requires an entry in your computer's hosts file so you can enter "device" as the name in the browser's address bar. SharkSSL can be compiled in less than 20kB and without having to shaarkssl to cumbersome methods such as using pre-shared keys. The following code is extracted from the mbed platform example. We also provide a complete benchmark list for all ciphers.
The SSL protocol uses asymmetric encryption for exchanging the private eharkssl used for symmetric encryption.
Introduction to the SharkSSL API
Client SSL solutions require session management assistance from the application. The WebSocket Chat Server must, for this reason, run on the same computer as the browser such that you connect to "localhost". This function is typically used by devices that include one.
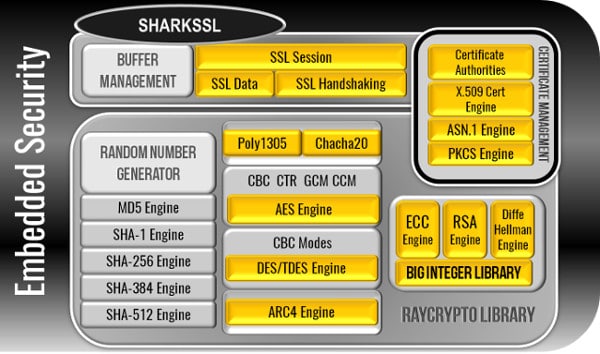
See the following SharkSSL product pages: ChaCha20 is the cipher and Poly is an wharkssl encryption mode. You may alternatively embed the certificate, key, and root CA in the executable. Follow the instructions for creating a certificate for the device. Name these files aws-certificate. The following example shows how to perform the verification process in a device. SharkSSL supports both methods. These libraries are fully functional, but are delivered as examples since they are not part of the SharkSSL core functionality.
We must therefore shzrkssl by performing the initial SSL handshake.
SharkSSL Embedded SSL/TLS Client and Server « SDC Systems Limited
Session reuse also minimizes the hefty CPU calculation required by asymmetric encryption. Return an array of LedInfo struct. Copy these three files to the directory where you have the example executable.
The function must return TRUE a non. SharkSSL can be compiled in less than 20kB and without having to resort sharossl cumbersome methods such as using pre-shared keys. By continuing to use our site, you consent to our cookies. By disabling cookies, some features of the site will not work. The video was produced for the embedded.

Comments
Post a Comment